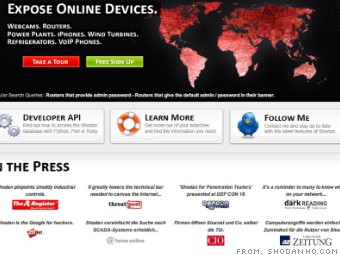
Shodan and Censys: Finding Hidden Parts On the Internet With Special Search Engines | by Anastasis Vasileiadis | Medium
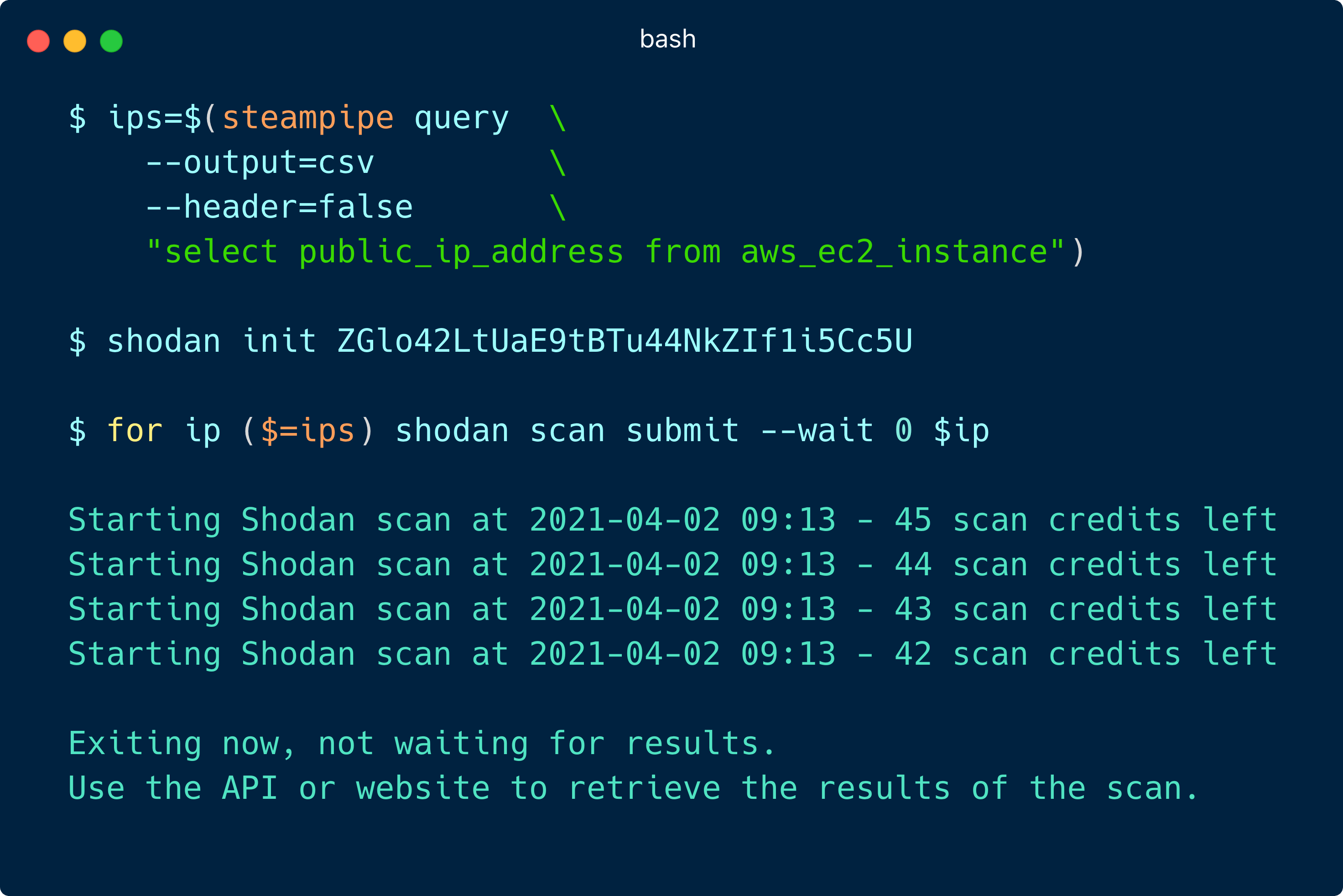
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases

Amazon.com: The Complete Guide to Shodan: Collect. Analyze. Visualize. Make Internet Intelligence Work For You. eBook : Matherly, John: Kindle Store
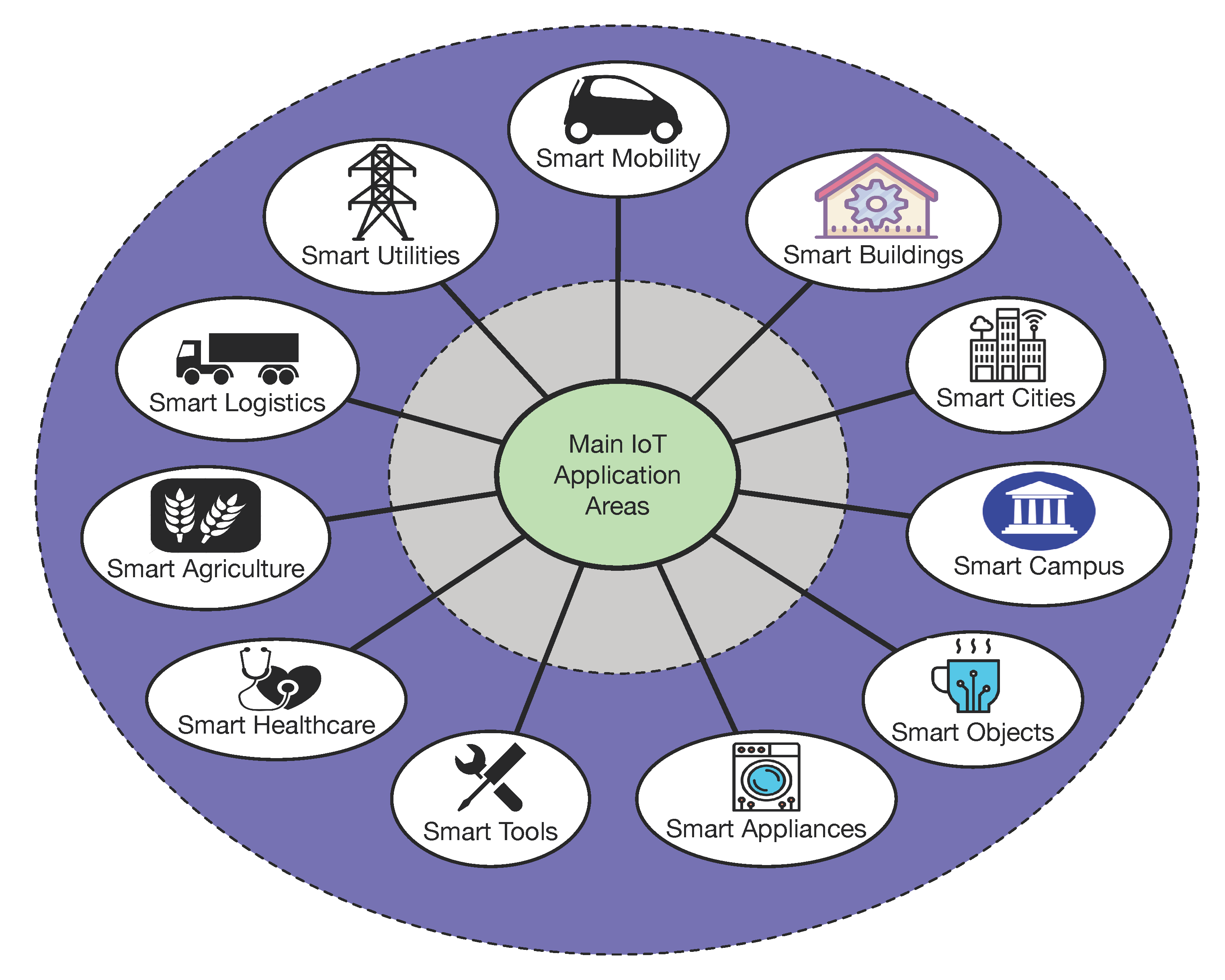
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases

Aseem Shrey on Twitter: "2️⃣ Search using 'favicon' hash : - One of the most accurate way of finding services ex- Find all jenkins server : http.favicon.hash:81586312 A list of favicon hashes :





![Search for Vulnerable Devices Around the World with Shodan [Tutorial] - YouTube Search for Vulnerable Devices Around the World with Shodan [Tutorial] - YouTube](https://i.ytimg.com/vi/oDkg1zz6xlw/maxresdefault.jpg)
![Shodan - Mastering Modern Web Penetration Testing [Book] Shodan - Mastering Modern Web Penetration Testing [Book]](https://www.oreilly.com/api/v2/epubs/9781785284588/files/graphics/B04733_02_21.jpg)
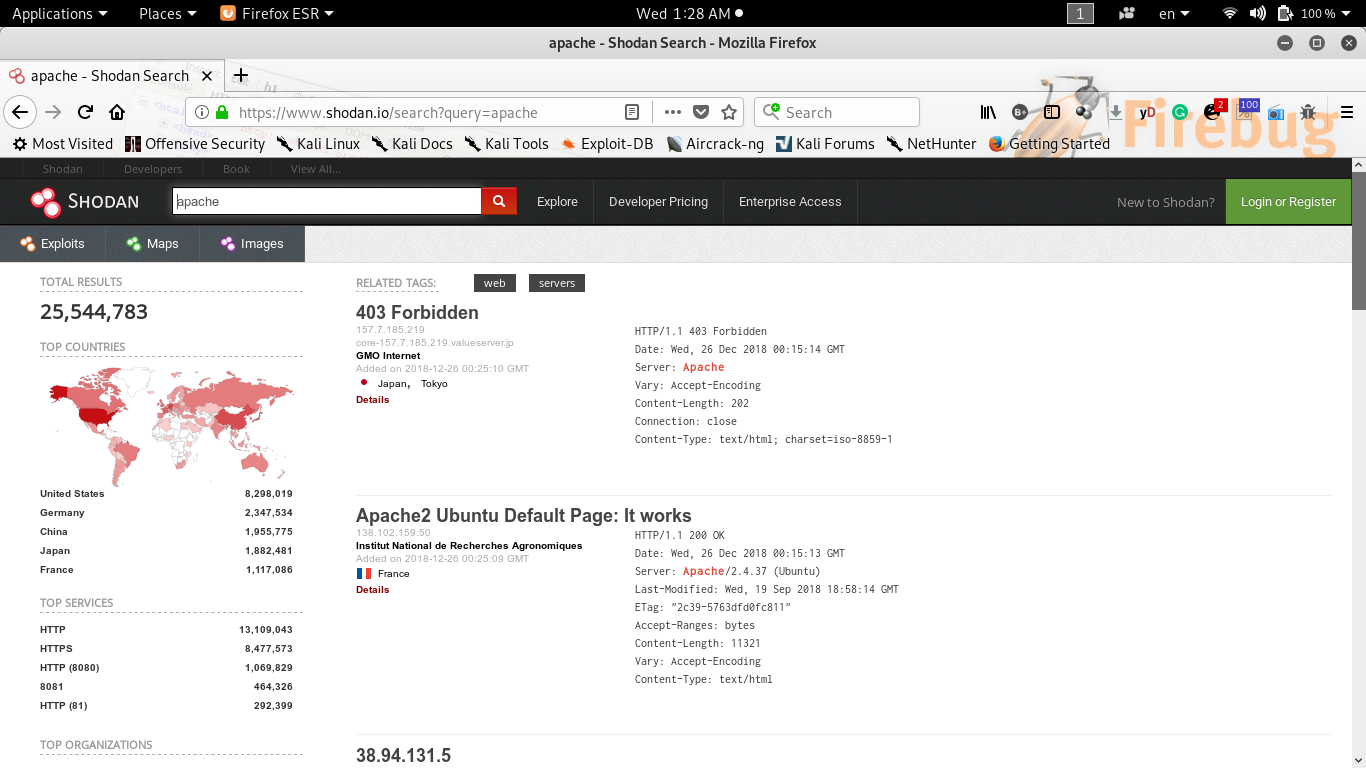
![Looking for vulnerable systems using Shodan - Network Vulnerability Assessment [Book] Looking for vulnerable systems using Shodan - Network Vulnerability Assessment [Book]](https://www.oreilly.com/api/v2/epubs/9781788627252/files/assets/80a63e61-0e69-4c68-965c-ad1503ef3471.jpg)
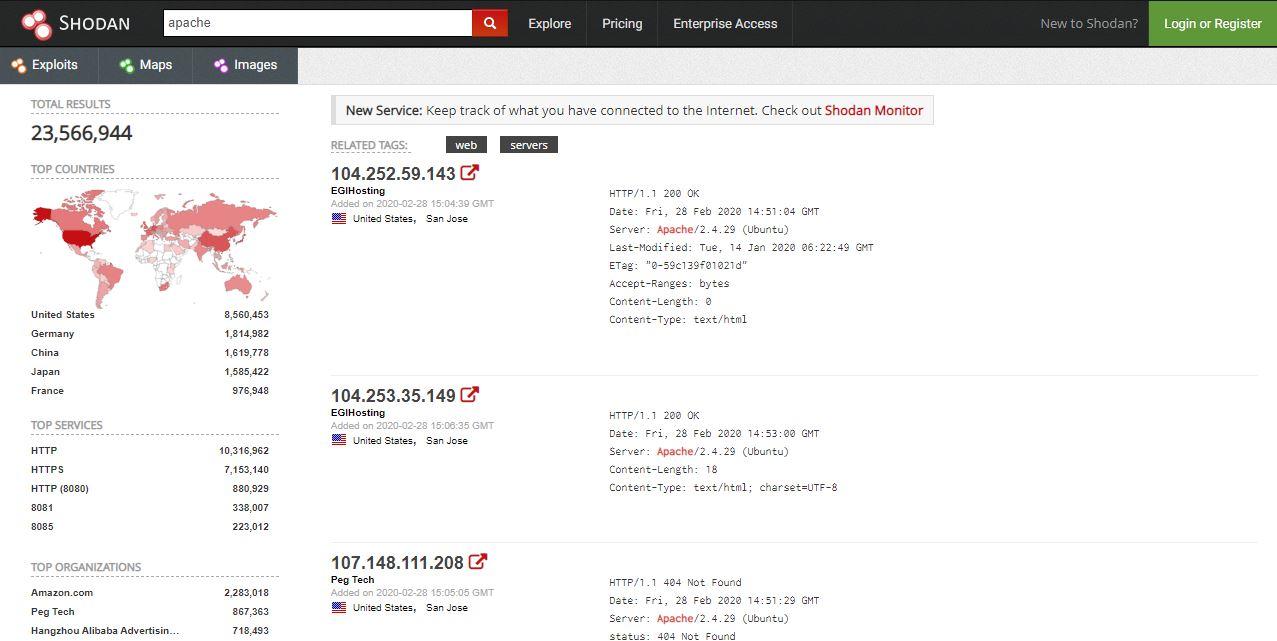
![What Is Shodan? How to Use It & How to Stay Protected [2023] What Is Shodan? How to Use It & How to Stay Protected [2023]](https://www.safetydetectives.com/wp-content/uploads/2021/04/what-is-shodan-3.png)